If you are not a LiveAction Maintenance Customer but would like to purchase a Maintenance contract for your LiveAction product please click here for sales information.
Category : Plug-Ins
Submitted By : Savvius
Downloaded : 194 Times
View Comments (1)
Deep in the dark corridors of Savvius Labs, we have developed a new capability called Filter Scripts for the Windows and Linux
Capture Engines that makes it possible for users to create filters that generate events and summary stats. It builds
on the existing filter and filter UI functionality to create arbitrarily complex conditions for
generating custom events and summary stats, as well as extract values and
strings out of the packets to create the text for the events and summary stats.
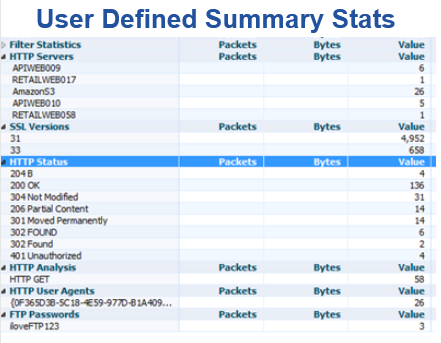
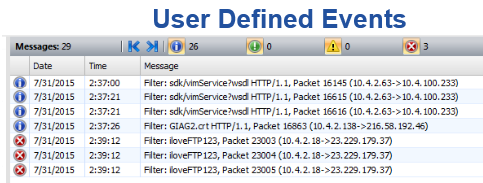
So how does it work? There are two parts to it. The first part is very simple, or at least familiar, since it is a feature we are all already used to: creating a filter. Just create an advanced filter with all of the filter nodes necessary to filter a particular type of packet. The filter could be for HTTP Response Code Packets, DNS Error Packet, SSL Version Packets, or virtually any other type of packet you can think of that has something your want to count or alert on.
The next step is to specify what the action should be if the filter is matched. This is easy as well since it is just another type of filter node. The filter node type is called the FilterEventPlugin, and it is one of the options available in the Analysis Module Filter Node list. By adding this node to the end of your filter node chain, you can now specify the action to be taken when a packet matches the preceding filter nodes.
Now comes the fun part, which is specifying the actions, and the various options for the actions. The action options are specified in the Comment field of the filter, along with the static text that will be used in the label or title of the action, which is to either generate an event and/or a summary stat.
Example
Alright, enough with the description, let’s see what it all
looks like. Below is a list of Filter Scripts in a filter folder called “Action Filters”. As the list of filters grows, there can be many different folders with many different types of filter scripts.
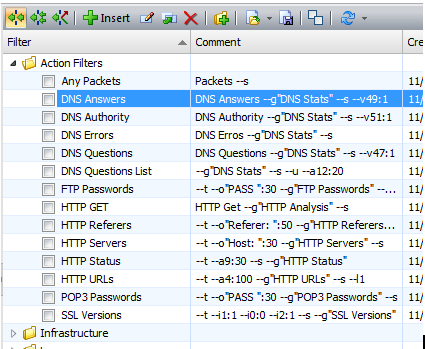
Let’s open one up.
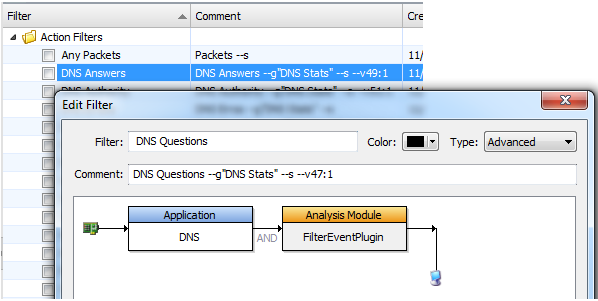
This Filter Script is called “DNS Questions”. The filter node is simple, just test for DNS. The next filter node is the FilterEventPlugin node, which in this case says to perform an action.
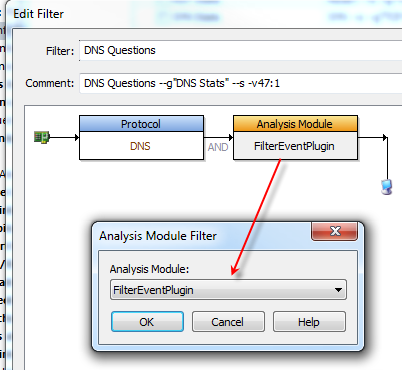
The action is specified as text in the Comment field. First is the static text of our action which is “DNS Questions”. In this case we have specified a –s, which means to generate a summary stat, we also use --g”DNS Stats” to specify the summary stat group to put it into. The next option is very cool. It is the –v, which says to extract 1 byte from offset 47 and use it to increment the value of the summary stat.
Here is the result:
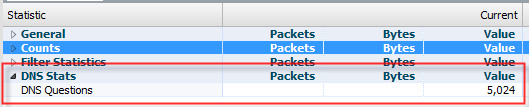
Do you see what we just did? We not only created a Summary Stat, but once it is there, then subsequent packets cause it to increment, either by 1, or by some value extracted from the packet.
And to go just a bit deeper, here is an example of a DNS packet showing the number of questions at offset 46
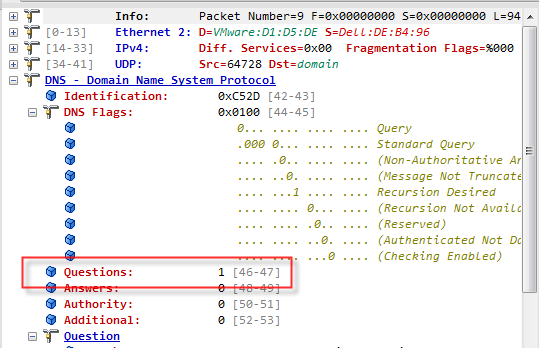
Options
Here is a list of the Filter Script options:
--iN:M
(extract and display integer with M bytes from N offset )
--aN:M
(extract and display string with M chars from N offset. Stops at nonprintable
character)
--vN:M
(like –i, but read binary M bytes as value to add to stats)
--o”pattern”:N
(read N ascii-bytes, after pattern “pattern” , attach to filterName)
--t
(if TCP, adjust “0-point” for offsets to tcppayload start instead of packet
start)
--u
(if UDP, adjust “0-point” for offsets to tcppayload start instead of packet
start)
--s
(enable summary stats)
--lN
(enable log entry with severity N)
--g”name” (stats group name)
On Windows, the files go here:
C:Program FilesSavviusCapture Engine
On Linux, they go here
/usr/lib/omni/plugins – FilterEventPlugin.so
/etc/omni – FilterEventPlugin.he