Cyber Security, and the Networks it has to Traverse
By Jim Thor – WildPackets Professional Services
Cyber Security news and articles seem to be written on a daily basis, and the attacks they talk about are happening even more often. The statistics are staggering, and although I will not go into them here, the numbers prove that this subject cannot be ignored.
So now it is time, once again, to talk about how you can know your environment, baseline the network, and prepare to find and understand anything which is outside the norm in your network. The first thing we must acknowledge is that these attacks are changing constantly, and by looking at what was found or identified historically, we would be missing every new attack (aka Zero Day attacks). Therefore, we will be using OmniPeek to find anything which is unusual.
To make sure we don't miss any new and unexpected behavior, we will use OmniPeek to validate normal expected behavior, and ignore it. By doing so, we will then have a capture (and reporting) on just the traffic and network behavior that is out of the norm.
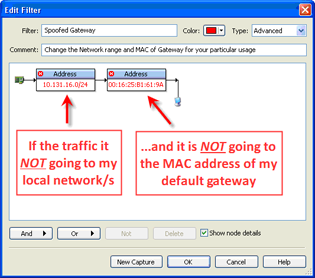
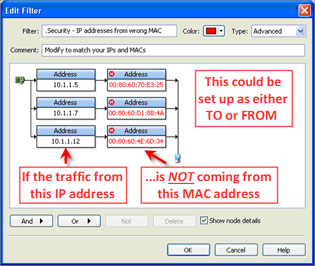
Let me show you a few examples to help illustrate what I mean. The first set of examples is to find a MiTM (Man in the Middle) or impersonation attack on any node or network segment. To do so, we must know both the IP address and MAC address of an end node to determine impersonation, or, to find someone spoofing a gateway, just the MAC address of the Gateway/Router for that segment. Here are the two filters I have made to alert us, both completed in seconds.
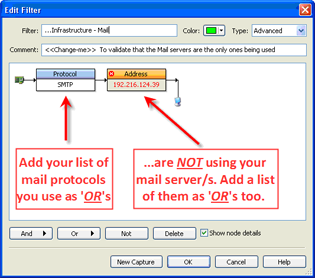
Another example of using this type of capture to identify suspicious activity would be to find Mail traffic destined for outside Mail servers, rather than the internal corporate mail servers. Although you could use this type of filter for any specific protocol or application traffic on your network, here is a simple filter to find outbound mail traffic not going to the corporate mail server. This is often an indication of viruses, worms or other malware present in the environment.
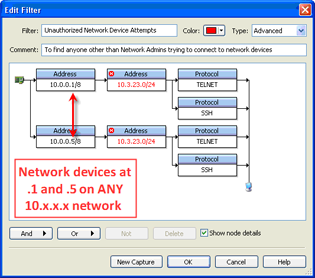
Another example of something out of the ordinary would be to watch for unauthorized users connecting to certain devices, like Network devices. This example would find Telnet or SSH traffic to any .1 or .5 in the 10.0.0.0 network, but not from the 10.3.23.0/24 network.
Although I could show you many more examples of these types of filters, the logic of what we are doing is much more important. Basically, "ignore all the traffic on your network that you know is normal, and only capture the traffic that is abnormal." If you capture ANY packets with these types of filters it means you have work to do, either to put an end to the oddity, or to modify your filter to avoid false positives.
To conclude, please remember, although we talked mostly about OmniPeek here, the same features are available in OmniEngines. And with the Forensics features of the Engines, these filters can be used historically to see what 'has' been happening on your network. Now we have true 24x7 understanding of the networks, and the traffic traversing them, to help augment our Cyber Security initiatives.