How to Extract Uncommon or Nonstandard Network Flows
Jim Thor – WildPackets Professional Services
The purpose of this tip is to show you how to find and extract the network flows that use uncommon or nonstandard ports.
This is necessary because in today's networks we often run applications on non-standard or uncommon ports. The issue that can arise from this is that OmniPeek will not know how to define the traffic, and will usually classify it all at the next lower protocol layer, usually TCP or UDP. As an example, you may be running HTTP on various ports. For the traffic on port 80 (standard), it will be defined by OmniPeek as HTTP. For the HTTP traffic on other non-standard ports, it will generally be classified as TCP.
This tip will show you how to separate the traffic, so that you can take the next step if necessary, customizing OmniPeek so that those flows show up as specifically defined traffic. This tip will not cover customizing OmniPeek, but you can find a video about that on your MyPeek page.
The simple steps below will walk you through doing this, slowly. It is possible to do this in fewer steps, but you need to know where to start first; then you can take shortcuts as you find necessary. We will be focusing on TCP in this example.
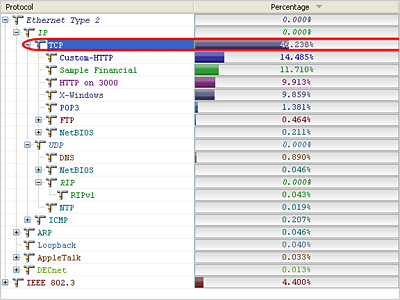
The first step is to 'Select Related' by the protocol (here TCP) and then 'Hide Unselected Packets' as you see below.
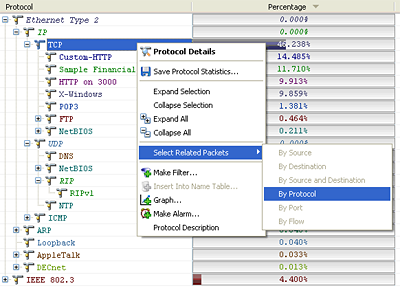
Once you have completed that, you will see that just the TCP traffic is left.
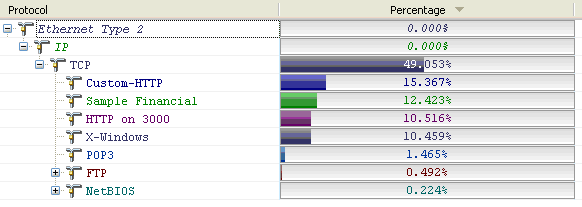
The next step is to highlight all the known traffic, and do a 'Select Related' by it. But this time you will 'Hide the Selected Packets'.
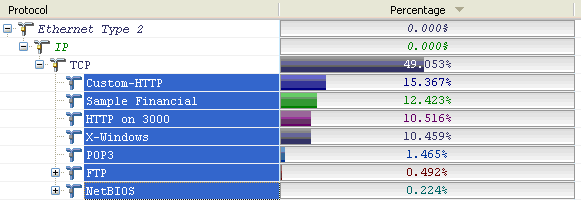
You now have just the TCP traffic that was running on those un-common or non-standard ports.
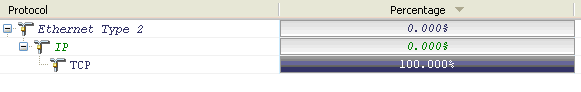
To get the flow information on this traffic now we will go to our Expert views, either Application or Flat depending on what you want to see.
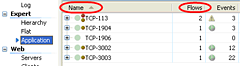
On the left side you see the 'Application Expert' which shows us the ports in use, and how many flows each port had. You can sort by the Name column (as shown here) or by the 'Flows' column to see the busiest ports. You could also use the 'Flat Expert' to see the individual flows and again sort according to what you are most interested in, generally the 'Server Port', but Server Address also has its benefits.
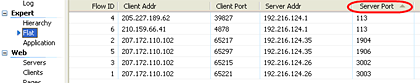
Now that you know the flows, you can take the next step and customize OmniPeek to identify this traffic specifically to fit your needs. It only takes a few moments to do this, and you will benefit greatly from it forever. Did you notice the custom protocols in the screen shots above?